Vérifiez le guichet automatique ou le terminal de place de vente : Avant d’insérer votre carte dans la fente, examinez attentivement le guichet automatique ou le terminal de position de vente.
In addition to routinely scanning your credit card statements, you'll want to put in place textual content or e-mail alerts to inform you about specified styles of transactions – including every time a acquire over an established amount pops up inside your account.
The material on this web site is accurate as of the posting date; on the other hand, some of our associate features might have expired.
ils m'ont envoyé une carte qui ne fonctionnait pas, et n'ont jamais voulu me rembourser ou me la changer. 750e dans le vent
The copyright card can now be used in the way a reputable card would, or for additional fraud like reward carding as well as other carding.
Dans certains cas, les fraudeurs utilisent également des microcaméras cachées ou de fake claviers pour capturer le code PIN de leurs victimes. Une fois que les criminels ont accumulateé ces informations, ils peuvent cloner la carte et l’utiliser pour retirer de l’argent ou effectuer des achats non autorisés.
L’un des groupes les furthermore notoires à utiliser cette approach est Magecart. Ce collectif de pirates informatiques cible principalement les sites de commerce électronique en insérant des scripts malveillants dans les systèmes de paiement en ligne. Ces scripts interceptent les informations de carte dès que l’utilisateur les saisit sur le web-site.
These consist of extra Superior iCVV values as compared to magnetic stripes’ CVV, and they cannot be copied making use of skimmers.
Comme des criminels peuvent avoir installé des micro-caméras près du comptoir dans le but de capturer le code solution de votre carte, couvrez le clavier où vous saisissez votre code PIN avec votre autre principal. Choisissez des distributeurs automatiques fiables
Whilst payments have gotten more quickly and more cashless, ripoffs are obtaining trickier and more challenging to detect. Among the most significant threats right now to enterprises and folks During this context is card cloning—exactly where fraudsters replicate card’s details with no you even recognizing.
Lastly, Permit’s not forget about that this sort of incidents may make the individual come to feel susceptible and violated and substantially impression their mental overall health.
Every chip card has a magnetic strip to be able to still make buys at retailers that haven't but mounted chip-looking through equipment.
Credit card cloning refers to carte clonée c est quoi developing a fraudulent duplicate of a credit card. It comes about every time a crook steals your credit card information, then works by using the knowledge to produce a faux card.
We’ve been very clear that we hope companies to use applicable guidelines and direction – together with, but not restricted to, the CRM code. If problems arise, organizations really should attract on our guidance and past choices to achieve good results
 Edward Furlong Then & Now!
Edward Furlong Then & Now! Mr. T Then & Now!
Mr. T Then & Now!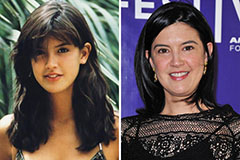 Phoebe Cates Then & Now!
Phoebe Cates Then & Now!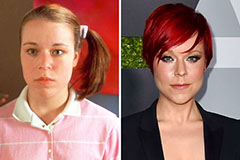 Tina Majorino Then & Now!
Tina Majorino Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now!